Cyber-Secure Tactics for Your Star Team
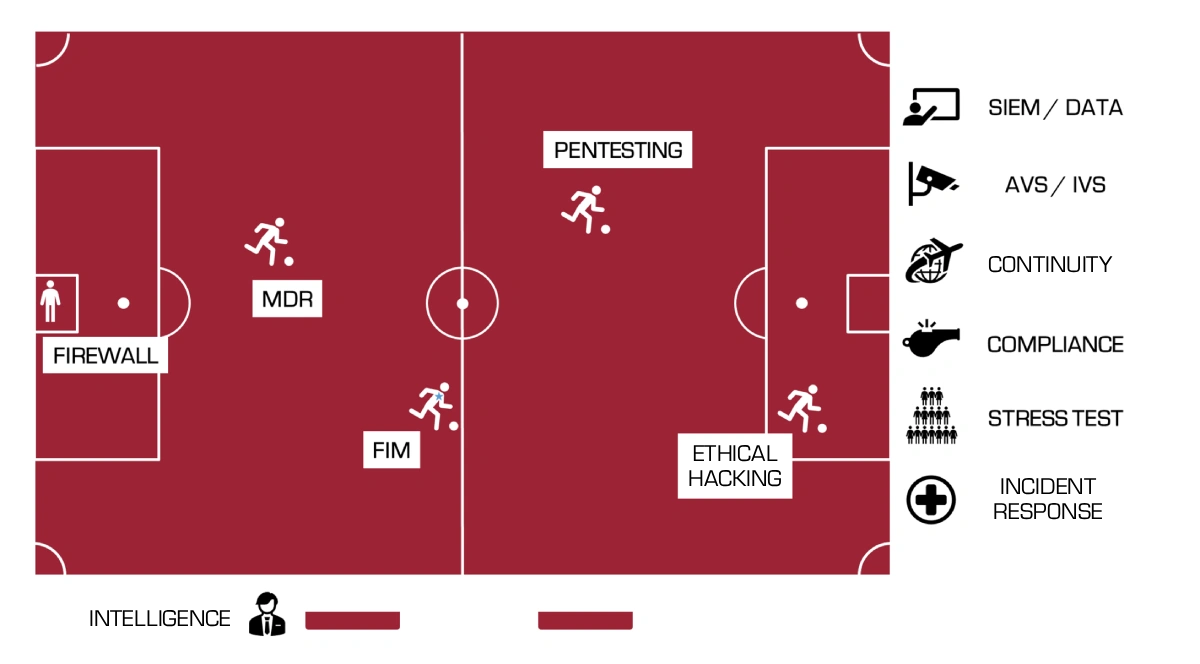

Understanding who does what in the world of cybersecurity is essential to protecting our goal: information. To help decipher the not-always-simple playing field of cybersecurity disciplines, at BOTECH we wanted to shed some light by translating technical jargon into the tactics and passion of something almost everyone knows: football.
Given that the current women’s national team world champion is Spain, we’re not only proud to “wear their jersey”, but we will also explain everything using a women’s team, debunking the myth that cybersecurity is a man’s field. So, without further delay, let’s get to the kickoff.
We begin our journey, as it couldn’t be otherwise, in the goal. This is the last stronghold before the ball crosses the goal line. The firewall is our star goalkeeper: agile, always alert, and ready to block any unexpected shot that cyberattackers launch in an attempt to score against us.
Moving into the defensive area, we find Managed Detection and Response (MDR), from which we protect each endpoint in our organization, assess the risks of every approach to the area, and, if necessary, patch (always kindly) any gaps in our lines.
File Integrity Monitoring (FIM), like a good team captain, is tireless, has exceptional peripheral vision, and is always ready to intercept and clear any advance before it becomes a real threat. It ensures there are no unexpected tactical changes and that every piece fits exactly as it should.
They are our most skillful wide players, capable of dribbling through every layer of security using refined and innovative techniques to find weaknesses through which an opposing attacker could slip in. Always keeping their heads up, they can spot the perfect pass or shot as soon as the opportunity appears.
She is the specialist in scoring in the smallest, busiest, and most demanding areas on the pitch: the boxes. Fast as lightning, she positions herself at the doors of the goal knowing her ability to anticipate the defenders’ movements. All of this, of course, to teach us how to strengthen our own lines.
On the sidelines stands our technical director, cyberintelligence. This strategist knows every move the opponent will make before it happens and adjusts our tactics to counter their strategies, keeping us always one step ahead. She can read and define every match, give precise instructions to cover security holes, and identify where they are “trying to tickle us” (dark and deep web).
Off the field, but deeply involved, is our expert team dedicated to analyzing and synthesizing large volumes of data to provide strategic insights, allowing us to make decisions based on detailed information and analysis, particularly regarding information security events.
Beyond the players, it is necessary to have security teams that ensure a good experience for both the audience and the teams, as well as all staff involved in a major match. This team performs internal and external scans that prevent unwanted elements from entering the stadium.
No team becomes world champion without specialized support in all logistical matters, including travel and stays away from home. Equipment, supplies, maintenance, and communications are, among others, essential conditions to win in this “sport” of cybersecurity.
As the classic saying goes, football is 11 against 11 players (women, in this case) wearing short tracksuits, watched and directed by another person dressed in black who scolds them. More than “scolding”, the referee is there to ensure that everyone plays according to shared and common rules, without tricks or shortcuts, and to call out fouls when they occur.
A major sporting event also needs access systems that allow tens of thousands of fans to enter the stadium. Our specialists simulate possible collapse scenarios through load tests, such as DDoS attacks.
Like trained medical units ready to treat any injury immediately, our incident response plans are designed to handle “injuries” to the IT system, ensuring a fast and effective recovery to maintain the “health” of our clients’ technological infrastructure.
The main difference between football and cybersecurity is that the latter is a game with no final whistle: it is played 24/7, in a world where opponents never tire. But with this star lineup and a well-defined strategy, your team will be ready to face every challenge and come out victorious.
BOTECH’s graphic approach not only seeks to make cybersecurity more accessible; it also imparts a crucial lesson: just like in football, teamwork, preparation, and strategy are essential for security. So even if not all of us can be football stars, with this approach we’ll have the keys to playing in cybersecurity’s first division.